Definition:
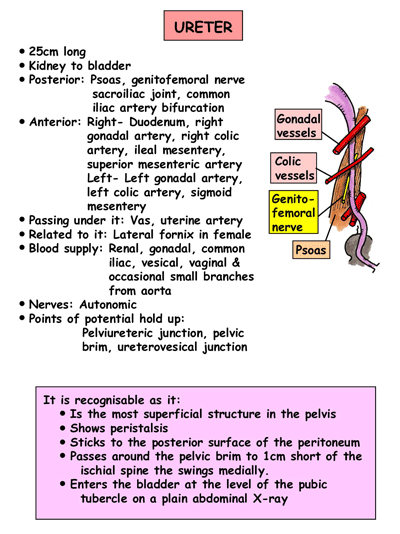
The ureters are a pair of muscular tubes which convey the urine from kidneys (renal pelvis) to the urinary bladder.
Size and Extent:
Retroperitoneal structure in the posterior abdominal wall (upper part) and lateral pelvic wall (lower part)
Parts, Courses and Relations:
A) Pelvis of Ureter:
A) 3 Anatomical Constrictions:
1. Abdominal part: Branches from Renal artery, Abdominal aorta and Gonadal artery
2. Pelvic part:
Nerve Supply:
From inside to outside
1) Mucosa:
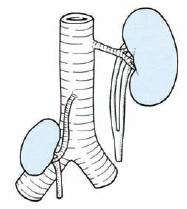 1. Ureteral duplication: The mesonephric duct may give off a double metanephric bud so that 2 ureters may develop on one side (Double ureter) or both sides (Bifid ureter). These ureters may fuse into a single duct anywhere along their course or open separately into the bladder
1. Ureteral duplication: The mesonephric duct may give off a double metanephric bud so that 2 ureters may develop on one side (Double ureter) or both sides (Bifid ureter). These ureters may fuse into a single duct anywhere along their course or open separately into the bladder
2. Ectopic ureter: Extra ureter may open ectopically into the vagina or urethra resulting in urinary incontinence.
3. Retrocaval ureter: Ureter deviates medially and passes behind the inferior vena cava, winding about and crossing in front of it from medial to lateral side. It may lead to right lumbar pain, recurrent urinary tact infections or episodes of acute pyelonephritis.
Detecting Ureteric Calculi:
 In searching for a ureteric stone on a plain radiograph of the abdomen, one must imagine the course of the ureter in relation to the bony skeleton. It lies along the tips of the transverse processes, crosses in front of the sacroiliac joint, swings out to the ischial spine and then passes medially to the bladder.
In searching for a ureteric stone on a plain radiograph of the abdomen, one must imagine the course of the ureter in relation to the bony skeleton. It lies along the tips of the transverse processes, crosses in front of the sacroiliac joint, swings out to the ischial spine and then passes medially to the bladder.
An opaque shadow along this line is suspicious of calculus. This course of the ureter is readily studied by examining a radiograph showing a radio-opaque ureteric catheter in situ.
Summary:
U Can Download Any Videos, All cracked Applications, Games in the net & also with Various Features.
Click Here to Try ScienceHack ToolBar...
The ureters are a pair of muscular tubes which convey the urine from kidneys (renal pelvis) to the urinary bladder.
Size and Extent:
- Length: About 25 cm (10 inches)
- Diameter: About 3 mm
- Extent: Pelviureteric junction to urinary bladder
Retroperitoneal structure in the posterior abdominal wall (upper part) and lateral pelvic wall (lower part)
Parts, Courses and Relations:
A) Pelvis of Ureter:
- Arises from the renal pelvis (leaves kidney from hilum situated medially) formed by calyces encircling the renal papillae
- Descends along the medial margin of the kidney
- At the lower end of kidney, it becomes continuous with the abdominal ureter
- Passes downwards and medially to lie on the medial edge of psoas major
- Then enters into the pelvis at the bifurcation of the common iliac artery in front of the sacroiliac joint.
- Anteriorly, the right ureter is covered at its origin by the 2nd part of the duodenum and then lies lateral to the inferior vena cava and behind the posterior peritoneum
- Right ureter is crossed by the testicular (or ovarian), right colic, and ileocolic vessels. The left ureter is crossed by the testicular (or ovarian) and left colic vessels
- Then passes above the pelvic brim, behind the mesosigmoid and sigmoid colon to cross the common iliac artery immediately above its bifurcation and enter the true (lesser) pelvis
- Runs downwards and backwards on the lateral pelvic wall in front of the internal iliac artery to reach just in front of the ischial spine
- Then turns forwads and medially to enter the urinary bladder
- In the male it lies above the seminal vesicle near its termination and is crossed superficially by the vas deferens
- In the female, the ureter passes above the lateral fornix of the vagina lateral to the supravaginal portion of the cervix and lies below the broad ligament and uterine vessels
- Passes obliquely through the wall of the bladder and open into it at the lateral angle of trigone
A) 3 Anatomical Constrictions:
- Pelviureteric junction
- Pelvic brim (Crossing of iliac vessels)
- Ureterovesical junction
- Pelviureteric junction
- Pelvic brim (Crossing of iliac vessels)
- Crossing of Vas deferens(♂) / Broad ligament(♀)
- Ureterovesical junction
- Ureteric orifice (Intravesical)
Comparison with Esophageal constrictions:Blood Supply:
Esophagus has 4 constrictions but ureter as 5 constrictions (surgical).
- Cricopharyngeal = Pelviureteric
- Crossing of aorta = Crossing of iliac artery
- Crossing of left main bronchus = Crossing of vas deferens/broad ligament
- Diaphragmatic hiatus = Ureterovesical junction
1. Abdominal part: Branches from Renal artery, Abdominal aorta and Gonadal artery
2. Pelvic part:
- As it crosses pelvic brim: Branches from Common Iliac and Internal Iliac arteries
- Inside the pelvis: Inferior vesical artery (Male) and Uterine artery (Female)
Nerve Supply:
- Sympathetic: T10-L1 spinal segments
- Parasympathetic: S2-S4 nerves
From inside to outside
1) Mucosa:

- Presents a few longitudinal folds giving its lumen a star shaped appearance
- Epithelial lining: Transitional epithelium
- Lamina propria: Fibrous tissue containing many elastic fibers, blood vessels and nerves
- Smooth muscles
- Upper 2/3 of ureter: Inner longitudinal and Outer circular fibers
- Lower 1/3 of ureter: Inner longitudinal, Middle circular and Outer Longitudinal fibers
- Fibrous connective tissue
- A portion of the ureter has serosa (mesothelium/simple squamous epithelium) covering it
- Mesodermal in origin
- Metanephric duct (Ureteric bud) appears as a diverticulum at the lower end of the mesonephric duct
- The metanephric duct (Ureteric bud) develops into the ureter, pelvis, calyces and collecting tubules
- On top of metanephric duct, later a cap of tissue differentiates to form the definitive kidney or metanephros which develops into the glomeruli and the proximal part of the renal duct system.
 1. Ureteral duplication: The mesonephric duct may give off a double metanephric bud so that 2 ureters may develop on one side (Double ureter) or both sides (Bifid ureter). These ureters may fuse into a single duct anywhere along their course or open separately into the bladder
1. Ureteral duplication: The mesonephric duct may give off a double metanephric bud so that 2 ureters may develop on one side (Double ureter) or both sides (Bifid ureter). These ureters may fuse into a single duct anywhere along their course or open separately into the bladder2. Ectopic ureter: Extra ureter may open ectopically into the vagina or urethra resulting in urinary incontinence.
3. Retrocaval ureter: Ureter deviates medially and passes behind the inferior vena cava, winding about and crossing in front of it from medial to lateral side. It may lead to right lumbar pain, recurrent urinary tact infections or episodes of acute pyelonephritis.
Detecting Ureteric Calculi:

Calculi in left ureter lateral to spine
An opaque shadow along this line is suspicious of calculus. This course of the ureter is readily studied by examining a radiograph showing a radio-opaque ureteric catheter in situ.
Summary:

U Can Download Any Videos, All cracked Applications, Games in the net & also with Various Features.
Click Here to Try ScienceHack ToolBar...
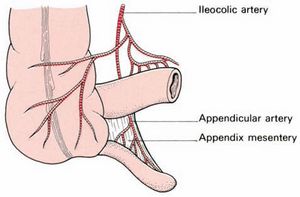
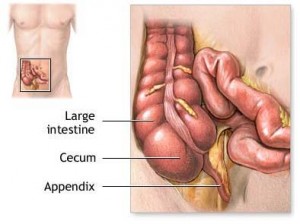 Also called as vermix, vermiform appendix is a narrow vermin (worm shaped) tube arising from the posteromedial aspect of the cecum (a large blind sac forming the commencement of the large intestine) about 1 inch below the iliocecal valve. Small lumen of appendix opens into the cecum and the orifice is guarded by a fold of mucous membrane known as ‘valve of Gerlach’. The 3 taenia coli (taenia libera, taenia mesocoli and taenia omental) of the ascending colon and caecum converge on the base of the appendix.
Also called as vermix, vermiform appendix is a narrow vermin (worm shaped) tube arising from the posteromedial aspect of the cecum (a large blind sac forming the commencement of the large intestine) about 1 inch below the iliocecal valve. Small lumen of appendix opens into the cecum and the orifice is guarded by a fold of mucous membrane known as ‘valve of Gerlach’. The 3 taenia coli (taenia libera, taenia mesocoli and taenia omental) of the ascending colon and caecum converge on the base of the appendix.
 extremely variable. The appendix is the only organ in the body which is said to have no anatomy. When compared to the hour hand of a clock, the positions would be:
extremely variable. The appendix is the only organ in the body which is said to have no anatomy. When compared to the hour hand of a clock, the positions would be: