Step 1: Get a keylogger There are many great keyloggers out there, however my favorite is Project Neptune and I will be using it for examples and designing my presentation around the settings Project Neptune provides. It has a very helpful user friendly interface and is very reliable in my, very narrow and premature, opinion. Link:
neptuneNow I have nothing against any other keyloggers and, as much as it shames me, have not tried any other keyloggers. Any should work, although Project Neptune comes with a binder which is very helpful and I'm not sure that many other keyloggers do (but I could be wrong).
Step 2: Setting up the keylogger-Settings 1 * Keylogging-For Project Neptune you have 2 options for reviving the logs of you slave. Email is pretty basic; however depending on how well you spread your keylogger, you might notice your mailbox getting a little too full. FTP stands for File Transfer Protocol, a method of transferring files over the internet (hence the name

). To do this you'll need an FTP client. I never got into FTP so I just stuck with email.
Next you get to choose the intervals that you receive logs at. I highly advise you do not go less than 20 minutes. Your mailbox will become painstakingly cluttered (especially if your slave somehow sets up the keylogger multiple times on their computer) with anything less. When you get multiple people keylogged you will thank me for this.
Logging the text on the clip board is also very handy. You might notice in your logs that the user typed "[ctrl] v [/ctrl]". Whenever you see that, go up to the clip board and that is what should be in place of the sequence.
Logging the user's specs is not necessary. However, I like to check out how much RAM people have. It humors me to see people with only 1 gig of RAM or on the contrary with 40 or so but with only a 2GHz processor. But that's just because I'm extra creepy.

Email settings can be confusing. I recomend making a gmail account just because Project Neptune provides the SMTP sending server and port. It is possible to use a yahoo/hotmail/live/comcast/whatever email but you need to provide your own SMTP information; which I couldn't get to work to save my life. Most email service's SMTP info can be found via search engine. The rest is self explanatory. THE EMAIL TO SEND AND RECEIVE KEYLOGS BOTH BELONG TO YOU! I know it sounds dumb but I thought one of them had to be my slave's email. It is not. Please don't tell me how dumb I was, because I already know.
Unless you are using an FTP server, you can leave the FTP settings blank. Here's an example of my settings:
![[Image: Keylogging.jpg]](http://i1088.photobucket.com/albums/i336/nck0099/Keylogging.jpg)
-Settings 2 * System Wide-This section of Project Neptune is used to limit the defenses of your slave. If he/she is task manager savvy and is able to identify suspicious processes, they might be able to disable the keylogger. However, if you make your keylogger very subtle, they will most likely not even notice they are being keylogged (unless you are harassing them, changing their facebook pictures, deleting game accounts, taking money from bank accounts/paypal, ect). I prefer to not disable anything. I was keylogged and the only reason I knew was because my task manager was disabled. I googled the most likely cause and found out it was due to a keylogger. If my task manager was still available to me, I probably wouldn't have noticed until all of my game accounts and credit cards were stolen. So don't make the same mistake my predator did.
Example of my settings:![[Image: 1.jpg]](http://i1088.photobucket.com/albums/i336/nck0099/1.jpg)
-Settings 3 * Instillation-This section is not very difficult to navigate. Basically, make it so that the keylogger runs on startup for all users (option 2). It doesn't really matter where the keylogger is stored. If the file the keylogger is bound to is legit, then do nothing to it. This makes it very subtle. The keylogger is in the back and the slave has the download they wanted. For file downloading, I'm not quite sure what it's purpose is. And it most not be very important if I was able to successfully keylog multiple people without using it. Here's an example of my settings:
![[Image: 2.jpg]](http://i1088.photobucket.com/albums/i336/nck0099/2.jpg)
-Settings 4 * Extra Options-I find this section very helpful. To be honest, I'm not quite sure when the fake error message pops up. It's not seen in the picture but to the end of mine I added "It is recommended that you restart your computer now." For whatever reason the error message pops up, when the user restarts their computer, the keylogger is re-initiated, which resolves any problems it was having.
The self destruct option is very convenient. You can only take so much from a person. Once you've stolen all of their game accounts, or whatever it is you are after, then the logs just get annoying. Set this to however long you feel necessary to get what you're after.
Screen shots are a must. They explain the confusing keystrokes. For example, my log was showing me random letters all jumbled up. I was so confused. Turned out my host was playing some word game on the internet which was clarified through the screen shots. Really all you have to do is click send at the same time as your logs. However I also did the option to set it to send every 20 minutes, just like my text logs. All this did was double email me the same image. One a text log with a SS attached, the other a blank message with a SS attached.
Example of my settings:
![[Image: 3.jpg]](http://i1088.photobucket.com/albums/i336/nck0099/3.jpg)
-Settings 5 * Server creation-You don't have to list any server settings unless you really feel obliged to create a fake Microsoft Corp program (lol). I never did and mine turned out fine.
File pumping makes the file bigger. Say you are binding a keylogger to an empty .exe file because you're too lazy to get a real file, if you post this on the internet, it will be obviously fake. So you pump a couple megabytes into the keylogger (it really depends on the file, for ex a movie would almost a GB) and you're good to go.
Now to create your server, randomize the Mutex a few times, come up with a process name (or leave at iexplorer.exe) and click Generate new server (save it to your desktop). This creates a .exe file. Now open up the file binder and click and drag the server you just created AND a file you want it to be binded to. This means the file you want to post on the internet that works but has the keylogger installed in the background. In my screenshot I do not have the server I created in it too. (I used the screenshot to ask what i was doing wrong and was too lazy to take another). Next, right click and then left click on compile server (save this to your desktop too).
SUPER TIP: IF YOU ARE GETTING AN ERROR MESSAGE SAYING SOMETHING LIKE "Dissembler Lib, Version=1.0.0.0, Culture=neutral, PublicKeyToken=null - Cannot find the file", YOUR ANTI-VIRUS IS DELETING THE LIB FILE AND IT WILL NOT LET YOU GENERATE YOUR SERVER. TEMPORARILY DISABLE/UNINSTALL THE ANTI-VIRUS, THEN RE-EXTRACT THE LIB FILE!
Example:
![[Image: 4.jpg]](http://i1088.photobucket.com/albums/i336/nck0099/4.jpg) Step 3: SPREAD
Step 3: SPREADNow go and upload the new file onto mediafire and spread the link! Whore this out everywhere. Forums, youtube video descriptions, Facebook (depending on how evil you are and you are willing to back-stab your friends), ect.
Note: I M against the use of hacking tools it is just for education only
U Can Download Any Videos, All cracked Applications, Games in the net & also with Various Features.
Click Here to Try ScienceHack ToolBar...

 Javascript is an object oriented scripting language.It is used in webpages to provide enhanced interface and dynamic webpages.It is mainly used as client-side scripting language.There are some cool javascript tricks that will blow your mind.You don’t need any programing knowledge to use these tricks.They can be used in any browser like Firefox,Google Chrome,Internet Explorer,Opera etc
Javascript is an object oriented scripting language.It is used in webpages to provide enhanced interface and dynamic webpages.It is mainly used as client-side scripting language.There are some cool javascript tricks that will blow your mind.You don’t need any programing knowledge to use these tricks.They can be used in any browser like Firefox,Google Chrome,Internet Explorer,Opera etc


 On the 4th of august at the world’s largest technical security conference – BlackHat USA 2011, which will take place in Las Vegas, SAP security expert and CTO of ERPScan Alexander Polyakov will show how any malicious attacker can get access to the systems running on SAP via Internet using new critical vulnerability.
On the 4th of august at the world’s largest technical security conference – BlackHat USA 2011, which will take place in Las Vegas, SAP security expert and CTO of ERPScan Alexander Polyakov will show how any malicious attacker can get access to the systems running on SAP via Internet using new critical vulnerability. ). To do this you'll need an FTP client. I never got into FTP so I just stuck with email.
). To do this you'll need an FTP client. I never got into FTP so I just stuck with email.
![[Image: Keylogging.jpg]](http://i1088.photobucket.com/albums/i336/nck0099/Keylogging.jpg)
![[Image: 1.jpg]](http://i1088.photobucket.com/albums/i336/nck0099/1.jpg)
![[Image: 2.jpg]](http://i1088.photobucket.com/albums/i336/nck0099/2.jpg)
![[Image: 3.jpg]](http://i1088.photobucket.com/albums/i336/nck0099/3.jpg)
![[Image: 4.jpg]](http://i1088.photobucket.com/albums/i336/nck0099/4.jpg)

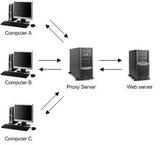 Hi Break the security readers, in my last post, introduced "Hide The IP" software. "Hide The IP" is best IP hiding software. The drawback of this software is cost. My one of reader comment "this is best software but it is costly to buy end users". So i am here going to guide you how to hide your IP address manually.
Hi Break the security readers, in my last post, introduced "Hide The IP" software. "Hide The IP" is best IP hiding software. The drawback of this software is cost. My one of reader comment "this is best software but it is costly to buy end users". So i am here going to guide you how to hide your IP address manually. 













